Contact ITS
Need Tech Support?
Know the rules
All NAU employees and students should read and be familiar with the Appropriate Use of IT Resources policy.University IT Policy Manual
Data Classification
*For the full policy and list of examples of each data type, review the Data Classification and Handling Policy.
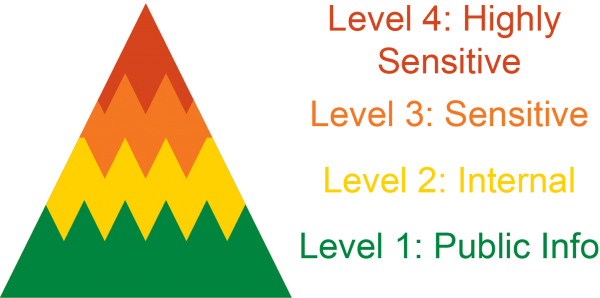
Level 1: Public Info Accordion Closed
Data that is generally available and intended for public use. This information may be freely distributed to all units and University Community Members as there is no concern for unauthorized use.

Examples Include: Campus maps intended for public use, public calendars, directory information (if not marked as restricted), factual reporting required by law, etc.
Level 2: Internal Accordion Closed
Data that is not generally available to the public or parties outside of the University. Risk of disclosure and harm to the University is low, but info still should be protected.

Examples Include: Prospective student data, University financial or budgetary information, network diagrams, building blueprints, UserIDs, etc.
Level 3: Sensitive Accordion Closed
Private information intended for restricted use within the University. There is a high level of risk associated with these data types, and they must be substantially protected from unintended or unauthorized use.

Examples Include: Student non-directory data, date of birth, employee information, personally identifiable information, limited data sets, security camera recordings, etc.
Level 4: Highly Sensitive Accordion Closed
Most confidential and sensitive data possessed or controlled by the University. Intended for extremely limited use consistent with substantial legal requirements for its protection and stewardship.

Examples Include: Human subject research, research involving vulnerable populations, healthcare data, controlled information, payment card data, etc.